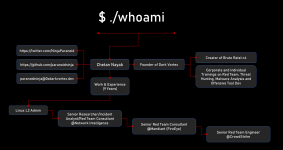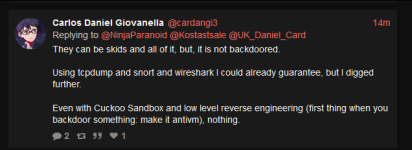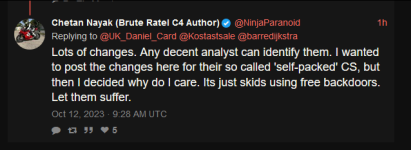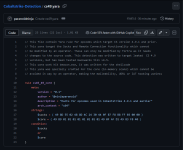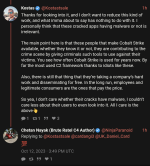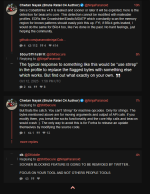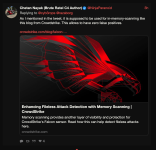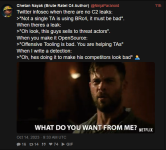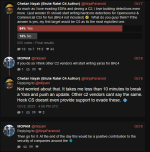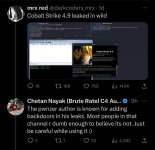
This is a great opportunity for Chetan's career and reputation - he has volunteered to provide proof of a backdoor (let alone "backdoors") in any Pwn3rzs "leak". How exciting! A real-life "malware analyst" with all sorts of bragging rights ought to knock this one out of the park! :) Right?
Fortunately this forum is wide open to anyone who wants to join, and the resource section is filled with files for him (and the entire community of malware analysts and security experts) to analyze. The telegram channel https://t.me/pwn3rzs is likewise open for anyone to join, and if you click on the files section there, it has 267 files! Golly, that is an awful lot of "leaks"! Should be pretty easy for a superstar gooner like Nayak to find just even one single file that is "backdoored" and show the world his proof. No problem! We are here with popcorn, watching each day to see his progress. Maybe he'll have some excuses or a slow start because he has to hurry up and learn a little about reversing? Maybe learn how to fire up a network sniffer and then install the so-called "backdoored" releases and then capture some packets? It's ok, we're sure he'll figure out how to use basic tools eventually. After all, he worked for Crowdstrike, and Mandiant, and now makes an overpriced c2. Maybe there is a reason he no longer works for Crowdstrike or Mandiant? Could it be he are wasn't smart enough to understand when something was actually backdoored or not? Or.. maybe he knows all about backdooring things, like he had claimed to backdoor Brute Ratel? Maybe he fiddled some customer data at Crowdstrike or Mandiant? Companies should take care in hiring companies that have the poor judgement of hiring people like this.
Looking forward to your malware analysis, Chetan "NinjaParanoid" Nayak! .. waiting ..
edit: for those that don't use twitter/x like me, one way to watch that thread:
https://nitter.net/NinjaParanoid/status/1711578873912299589#m
pdf capture attached (2023, Oct 11)
Attachments
Last edited: